Data security is by far one of the topics that we have been asked to help with the most. One of the solutions we usually adopt is to encrypt the Tableau Servers hard drivers and make the Tableau communication secure using TLS.
Tableau has now added the option to also encrypt your extracts – this means that users can now have an extra encryption on top of their service encryption. In practice this implies that even if a third party is able to access to a system this third party will not be able to open the .hyper files.
As you can see in the picture below, you have 3 options when setting up the Extract Encryption at Rest: Disabled, Enable “Allow users to optionally encrypt extracts on this site”, Enforce “All extracts published and stored on this site are encrypted”.
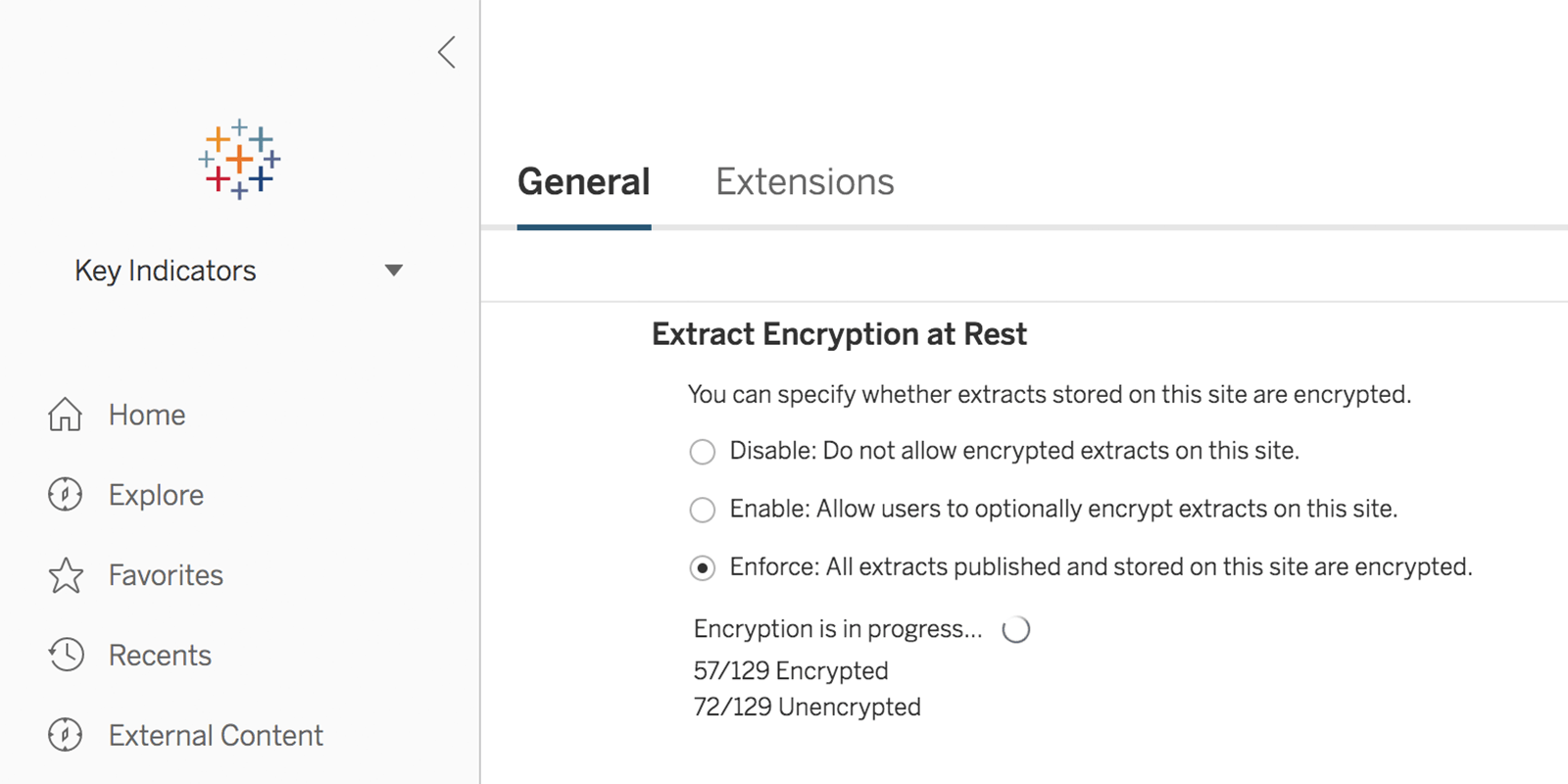
So, how does this feature actually work?
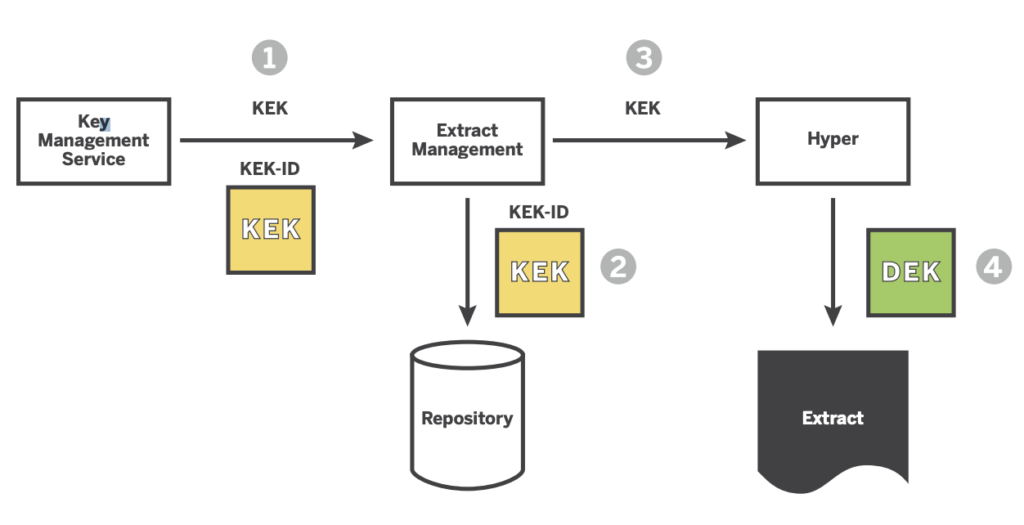
When the Tableau Data Engine (Hyper) starts its extractions it will first request a key (KEK) from the key management service (KMS). When this key is returned the extract management (EM) will tell the Tableau Data Engine to extract the data using the key it was provided.
After the extract is completed both the KEK and KMS will “forget” these keys as they will not be needed until the next extract will be created.
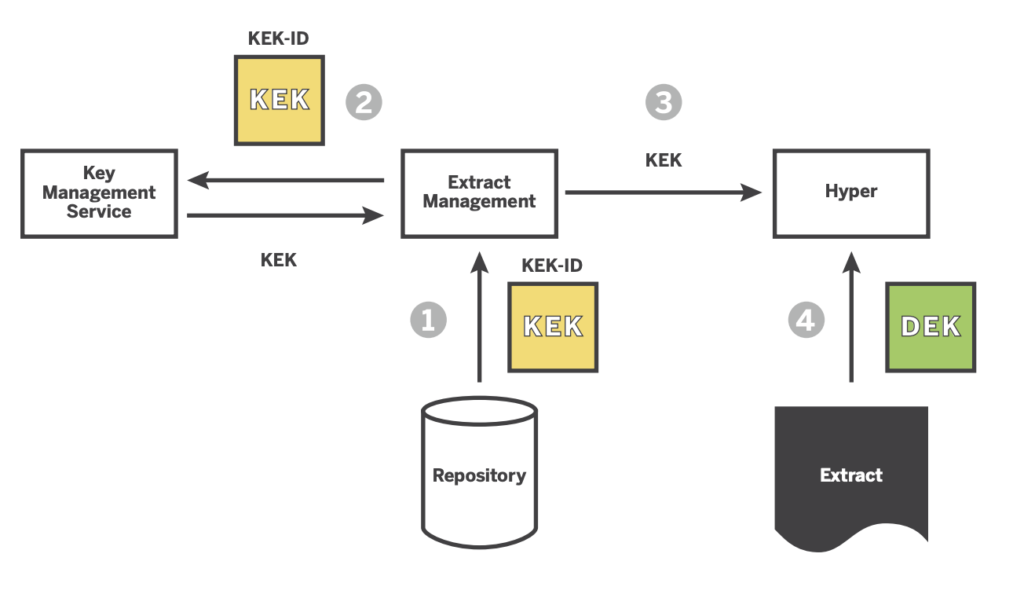
When the extract management wants to open the extract, it will retrieve the KEK-ID from the extract metadata stored in the repository. It will then ask (REQUEST?) the key management service (KMS) for the key linked to the KEY-ID. The key management service will then return this information to the extract management to open de hyper file, and then request the Tableau data engine (Hyper) to start extracting using the keys provided.
If you are interested in this topic and want to learn more, then you can always read more in this Tableau whitepaper “Encryption at rest”:
https://www.tableau.com/sites/default/files/whitepapers/encryption_at_rest_wp.pdf

